With digital security becoming a top priority for organizations of all sizes, Identity and Access Management (IAM) has emerged as an essential tool. As businesses strive to provide secure access to their networks and data, IAM systems simplify user authentication while keeping security strong. But how does identity management authentication actually work? In this post, we’ll look at what identity management is, how it addresses access and security needs, and the key benefits it brings to organizations.
What is Identity and Access Management?
Identity and Access Management (IAM) refers to the framework and policies used by an organization to control who has access to specific digital resources. In essence, IAM answers the questions: Who are you? and What should you have access to?
IAM systems create, manage, and monitor digital identities, which are essential for both security and user convenience. Through authentication (proving identity) and authorization (granting permission), IAM systems ensure that only verified users can access specific resources and perform certain actions. These solutions are commonly used for managing internal employee access as well as for external users, like clients or partners, in certain applications.
How Identity Management Solves this Problem
In an ideal world, every user would only access information they’re explicitly allowed to see, while unauthorized users are entirely blocked. However, managing access in real life is much more complicated, especially as organizations grow and adopt more tools, networks, and devices.
Identity management solves this challenge by centralizing the authentication and authorization processes. Here’s how:
- Single Sign-On (SSO): Rather than requiring users to remember different login credentials for every application, SSO allows users to authenticate once and gain access to multiple applications securely. This minimizes the need for multiple passwords, making it easier for users and more secure for IT departments.
- Multi-Factor Authentication (MFA): Identity management systems also enforce extra layers of security through MFA. This requires users to provide multiple forms of identification, like a password combined with a temporary code sent to their mobile device, reducing the risk of unauthorized access.
- Access Controls: IAM systems provide granular control over access rights, allowing IT teams to customize permissions based on users’ roles, groups, and other criteria. This means, for example, that someone in HR can access employee records, while someone in marketing can’t.
By authenticating users and managing permissions, IAM systems minimize security risks associated with unauthorized access, and they allow companies to scale securely and confidently.
What are the Key Benefits for Organizations to use Identity and Access Management (IAM) Systems?
- Enhanced Security: IAM systems are a powerful tool for minimizing unauthorized access and reducing the risk of data breaches. With features like MFA, SSO, and access control, IAM systems add multiple layers of security to sensitive information.
- Better Compliance: Many industries have strict regulatory requirements around data security and privacy. IAM systems help companies meet these standards by providing clear and trackable records of user access, making audits and regulatory compliance easier.
- Improved User Experience: IAM systems make accessing applications faster and easier, especially with SSO and self-service password recovery. This results in a smoother user experience, which is essential in today’s fast-paced work environment.
- Cost Savings: By simplifying user access and reducing password-related helpdesk calls, IAM systems can save organizations money in both IT resources and lost productivity. Additionally, automated access management can streamline onboarding and offboarding, reducing the risk of errors or delays.
- Scalability and Flexibility: As organizations grow, their IAM systems grow with them. IAM frameworks can support additional users and applications seamlessly, making them highly adaptable to the changing needs of a business.
Commonly Used Protocols by Identity Management Systems
Generally known as Authentication, Authorization, Accounting, or AAA, these identity management protocols provide standards for security to simplify access management, aid in compliance, and create a uniform system for handling interactions between users and systems.
Protocols
SAML. The Security Assertion Markup Language (SAML) protocol is most often used in systems employing the Single Sign-On (SSO) method of access control. In SSO, one set of credentials allows users to access multiple applications. This method is most beneficial when users must move between applications during sessions. Instead of requiring individual logins for each application, SSO makes use of data already authenticated for the session to streamline the switch between applications. The resulting increase in efficiency helps prevent bottlenecks in the authorization process. The Dotcom-Monitor platform supports SSO using SAML 2.0
OpenID. Like SAML, OpenID is used for web applications and can be seen in practice when interacting with products from Google and Yahoo! Implementation of this protocol is less complicated than implementation of SAML, making it more accessible for a variety of applications.
OAuth. Large customer-facing platforms like Facebook, Google, and Twitter rely on OAuth to connect third-party applications with the permission of users. OAuth works by allowing approved applications to use login credentials from one service or platform to provide access to additional applications without requiring separate logins. Authorization may be granted or revoked by the user at any time.
Let’s see how some of these protocols work in most commonly used identity management system these days Microsoft Azure Active Directory.
Identity Management with Azure Active Directory
Azure Active Directory (Azure AD) simplifies the way you manage your applications by providing a single identity system for your cloud and on-premises applications. You can add your software as a service (SaaS) applications, on-premises applications, and line of business (LOB) apps to Azure AD. Then users sign in once to securely and seamlessly access these applications, along with Office 365 and other business applications. The Dotcom-Monitor platform supports integration with Azure ADFS to set up user authentication and access.
SAML 2.0 Protocol
Azure Active Directory (Azure AD) provides SAML 2.0 protocol enabling applications to provide a single sign-on experience to their users. The SAML protocol requires the identity provider (Azure AD) and the application to exchange information about themselves.
The Application uses an HTTP redirect binding to pass an authentication request element to Azure AD (the identity provider). Azure AD then uses an HTTP post binding to post a response element to the cloud service.
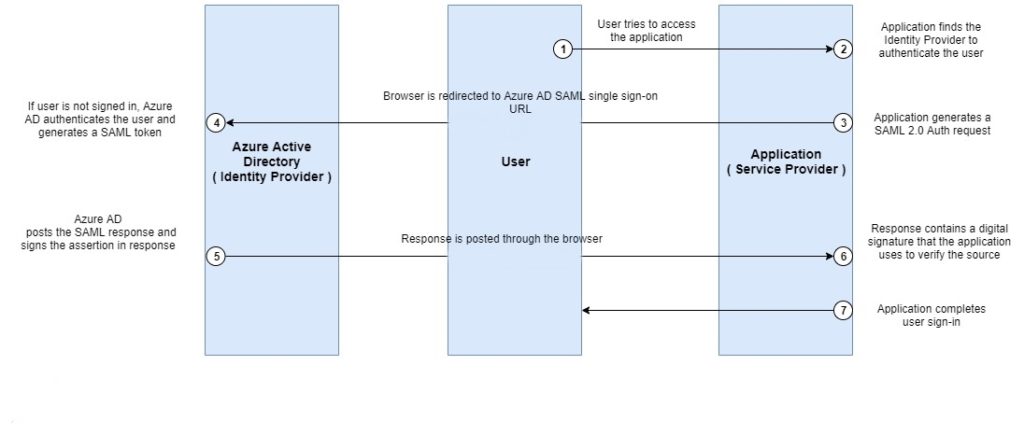
Authentication flow in SAML authentication:
- User tries to access the application by entering the application URL in the browser.
- The application then looks for the Identity Provider configured with it, which is SAML in this case.
- The application generates a SAML authentication request and user’s browser is redirected to Azure AD SAML single sign-on URL where user logs-in with credentials.
- Azure AD checks the valid credentials, authenticates the user, and generates a SAML token.
- Azure AD posts the SAML response containing the token and digitally signs the response, which is posted back to the application through the browser.
- The application verifies the response using the certificate provided to it and confirms the source.
- The application understands that the user is valid and completes the authentication allowing user inside the application.
OAuth 2.0 and OpenID Connect Protocols on the Microsoft Identity Platform
In nearly all OAuth 2.0 and OpenID Connect flows, there are four parties involved in the exchange:
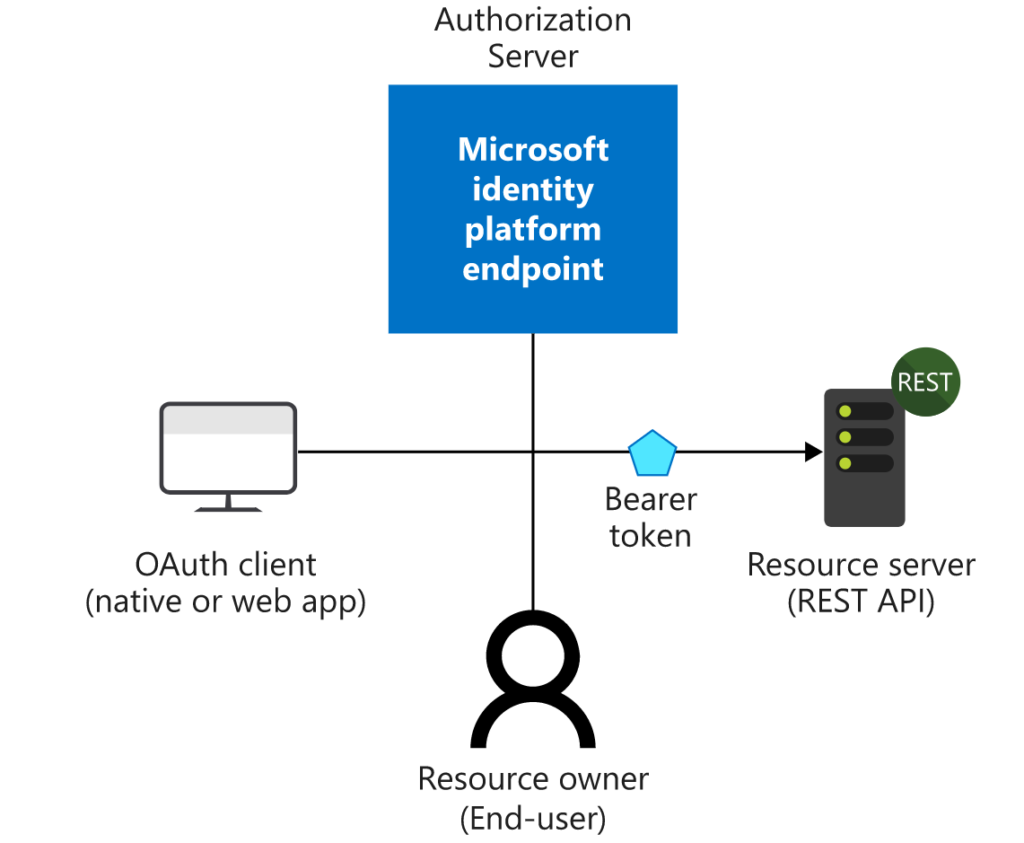
- Authorization Server. It is Microsoft’s Identity system and manages each user’s identity, granting and revoking access to resources, and issuing tokens. The authorization server also known as the identity provider. It securely handles anything to do with the user’s information, their access, and the trust relationships between parties in a flow.
- Resource Owner. It is the end user. It’s the party that owns the data and has the power to allow third parties to access that data or resource.
- OAuth Client. It is your application, identified by its unique application ID. The OAuth client is usually the party that the end user interacts with, and it requests tokens from the authorization server. The client must be granted permission to access the resource by the resource owner.
- Resource Server. Where the resource or data resides. It trusts the Authorization Server to securely authenticate and authorize the OAuth Client, and uses Bearer access tokens to ensure that access to a resource can be granted.
Authentication flow in OpenID:
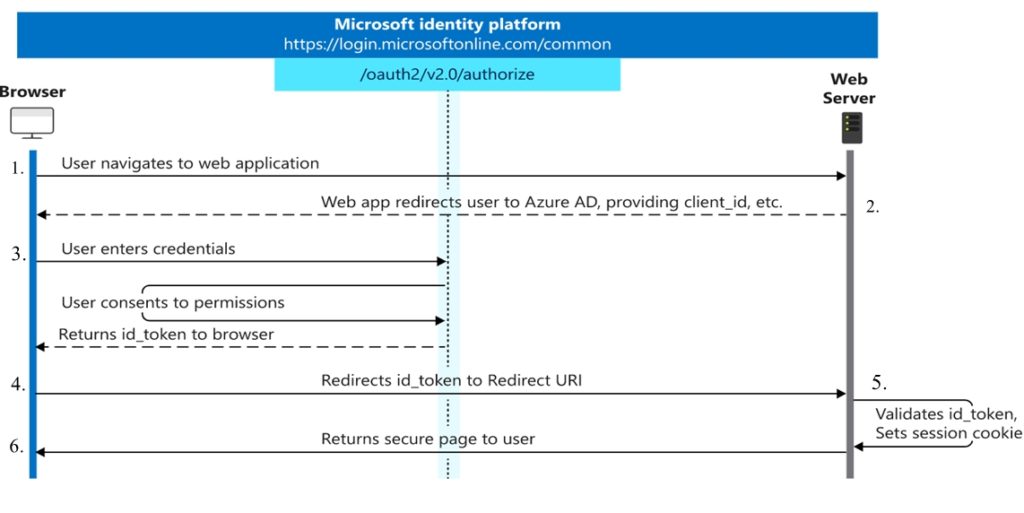
- User enters the application URL in the browser.
- The application is registered with Azure AD and has a unique application ID. The application redirects the user to Azure AD with the application ID so that the AD can identify the application and provides user with login screen.
- The user enters credentials to authenticate and consents to permissions. OAuth validates the user and returns a token to user’s browser.
- The user’s browser redirects the provide token to Redirect URI registered in Azure AD for their respective application.
- The application validates the token and sets the session, hence completing the authentication for the user.
- The user is securely signed in and allowed to access the application.
In Summary: Identity and Access Management
The objective of IAM is to ensure that authorized users have secure access to the necessary resources, like databases, applications, and systems. IAM simplifies processes for application owners, end users, and system administrators, ensuring they can carry out their essential duties quickly and effectively. Learn more about how Dotcom-Monitor supports IAM with third-party services integrations and SSO set up within the Dotcom-Monitor platform.

